Wednesday, September 23, 2009
How to Check Multiple Email Addresses for New E-Mail At Once-on yahoo or gmail or AOL
How to Check Multiple Email Addresses for New E-Mail At Once-on yahoo or gmail or AOL
"All Your Email Accounts in One Place
Zimbra Mail. Yahoo! Mail. Gmail. AOL. They all work automatically in Yahoo! Zimbra Desktop; even Outlook or any other work or personal email account using POP or IMAP is easy to set up. The best part—you can read them offline without an internet connection when you are in "airplane" mode".for More. information go to zimbra desktop features pageWindows 7 Facebook Gadget
Are you on facebook? Are you running Windows 7? More and more people can answer both questions with a clear “yes”.
You should definetly grab the facebook gadget for Windows 7 if you are on facebook a lot:

Windows 7 Facebook Gadget
It takes a little tweak to make it work, but it’s worth it.
Connect with us through Facebook!
Facebook’s popularity is exploding, their stocks are rising like crazy and there’s no end in sight.
I jumped on the bandwagon and I am proud to say that you can now connect with us through facebook. You can easily login using your facebook account. By the way, all data are stored only facebook servers, so it’s 100% safe to do that! Once you logged in you can post comments and access our member-only pages. Best of all, you can also login to our forums using your facebook account!
Download Facebook Sidebar Gadget
It’s a neat little gadget for your sidebar or your desktop. You can download the Windows 7 facebook gadget here:
How to make it work:
This one is a tricky one to get working, you have to add login.facebook.com and www.facebook.com into your IE trusted sites. Then you need to use the gadget to sign in and set the required permissions to allow it access to your facebook account. Not an install and go gadget like most, shame the writer hasn’t provided instructions. As for the gadget it seems quite useful, certainly saves logging in all the time or leaving facebook open permanently. Will use it for a time and see if its a keeper, does take up a large amount of space on the sidebar, could possible be smaller with more flyouts.
Logon Screens for Windows 7
Have you changed your logon screen already? There are many logon wallpaper around that will help you to tweak and customize your logon screen.
One of the best tools to change your logon screen on Vista and Windows 7 is LogonStudio by Stardock. It’s a free tool that comes in handy whenever you want to change your logon background.
You can download LogonStudio for free over at CNET:
LogonStudio Download @ CNET
It says “for Vista users”, but in this case it will run smoothly on your Windows 7 system as well. Windows 7 is using the same kernel as Vista that’s why there aren’t many compatibility issues anyway.
Download 1250 Logon Screens
Basically you can use your wallpaper collection for your logon backgrounds. If you don’t have a wallpaper collection, you should download our Windows 8 Wallpaper (1250 logon background wallpaper!).
Stardock’s LogonStudio
Stardock, the developer of LogonStudio, also offers a lot of great logon screens:








If you are interested in tweaking Windows 7 to it’s maximum, you should check out Stardock’s Object:
 | Object Desktop Ultimate |
Any real tweaker already owns it, it’s a package of the best tweaking utilities for Windows Vista and 7:
WindowBlinds (more Windows 7 themes), DeskScapes (Animated Wallpaper), DesktopX, SkinStudio (create your own skins and themes), ObjectBar (fancy docks, sidebars and more), etc.
Windows 8 Theme for Vista
The 22nd October is approaching quickly. That also means that we have to think about the successor of Windows 7, Windows 8.
We will soon launch Windows8themes.org – a site dedicated to Windows 8 themes & news.
Anyway, some designers are hard at work and have created an awesome visual desktop theme for Windows Vista that has been inspired by Windows 8.
Windows 8 Theme for Vista
Download Windows 8 theme
mufflerexoz from DA created this Windows 8 theme, you can freely download it here:
Windows 8 theme for Vista – Download
Windows 8 Release Date
Oh, I want to give out a warning. We can expect Windows 8 in 2012 or later, therefore there haven’t been any leaks at all and there won’t be any leaks for a while. That’s why you should stay away from any leaks for now, because they are all fakes and probably contain viruses and trojans.
We will keep an eye on any Windows 8 leaks and will inform you here. Of course we will also post any new Windows 8 themes and add them to our site. If you are a theme creator yourself, feel free to submit any themes to our site, either Windows 8 or Windows 7 themes. For Vista themes, you should go to our sister site vistadesktopthemes.com
Looking forward to the release of Windows 7 now! Hopefully Microsoft will keep up the good work and make Windows 8 even better.
Change Boot Order in Windows 7
Would you like to change the boot order in Windows 7? It’s very easy and doesn’t require a lot of work and you don’t have to modifiy the boot.ini, although you could do that as well if you are an advanced user, but let’s look at the safe & easy method first.
The “easy” method would be to change the default operating system by editing the startup settings.
Do you know where to change those options? No? Then read on…
About The Boot Order
The default OS will always be the first in your boot list. That’s why you have to change the the default OS if you want to change the boot order in Windows 7. Ifyou installed Windows Vista and then Windows 7, Windows Vista will be your default OS.
Why Do You Want To Change The Boot Order?
If the answer is “So that I can boot Windows 7″, then you should rethink your strategy. If you can only see the bootup options for a few seconds and you are not able to select Windows 7, then you don’t want to change the boot order, you want to change the boot selection time.
Set the time to 20 seconds, that will be enough to select the operating system of your choice. You will find that option directly below the dropdown-field of the default OS (compare with step 4.)
Changing The Boot Order In Windows 7
1. Open the Explorer (Windows key + E) and right-click on “Computer”
2. Click on “Properties”
3. Edit the Startup & Recovery settings as seen below:
Click on Settings ...
4. Next, you got to select the operating system of your choice from the dropdown field. I have highlighted it in the picture below:
Select the default OS from the dropdown field
Stock Gadget for Windows 7
Are you trading with stocks? Have you bought some Microsoft stocks or are you interested in DOW Jones and Co?
Well, the bad news are that Microsoft had to remove the stock gadget from Windows 7 RTM (all editions).
Dow jones, who is the provider of the “Dow Jones Industrial Average” quote feed to the Win 7 in-box stock gadget, wants a EULA agreement to be shown and accepted for any user before they can see the data from their feed in the stock gadget.
Luckily there are many 3rd party gadgets available.
Stock Gadget for Windows 7 (Windows 7 Beta)
I don’t fully understand why they had to remove the stock gadget. There are many sites that display realtime stats of Dow Jones, NASDAQ and other indizes, but I suppose it’s all about “pre-installation” without user confirmation. When someone visits a website and requests a realtime quote he does it on purpose and they have to agree to the EULA of the site. Did you know that you have to accept the TOS of a website or you are not “allowed” to visit a site? Of course no one cares, but I guess it makes all the difference.
Download Stock Gadget
Anyway, I hope that this stock gadget for Windows 7 helps your trading endeavours!
Almost 100,000 downloads. Pretty popular gadget by now!
Microsoft to release free security software soon
Microsoft plans to release the final version of its free antivirus software soon, according to a note sent to testers late Sunday.
"The final version of Microsoft Security Essentials will be released to the public in the coming weeks," Microsoft said in the note.
 (Credit: CNET News)
(Credit: CNET News)Microsoft first announced its plans for the product, then code-named Morro, last November, at the same time the company said it was scrapping its paid Windows Live OneCare product.
Public beta testing of Security Essentials started in June, with Microsoft reaching its goal of 75,000 testers just one day after it issued a call for them.
On a personal note, I've been using the product on several machines since June, and I like the way--unlike other antivirus programs--it doesn't make a spectacle of itself, just quietly doing its thing. I often forget it is running on a machine, yet it did save my bacon a couple weeks back when I almost caught Koobface from a friend on Facebook.
Firefox gets an early taste of 3D Web standard

A nascent technology called WebGL for bringing hardware-accelerated 3D graphics to the Web is getting a lot closer to reality.
Last week, programmers began building WebGL into Firefox's nightly builds, the developer versions used to test the latest updates to the open-source browser. Also this month, programmers began building WebGL into WebKit, the project that's used in both Apple's Safari and Google's Chrome.
Wolfire Games picked up on the WebKit move and offered a video of WebGL in action.
Overall, the moves stand to accelerate the pace of WebGL development by making it easier to try out. But the technology still has a ways to go before people will be able to play Web-based versions of a 3D software such as first-person shooter video games or Google Earth.
"All of these implementations are going to have some interoperability issues for the next little while, as the spec is still in flux and we're tracking it at different rates, but will hopefully start to stabilize over the next few months," said Vladimir Vukicevic in a blog post.
WebGL is one of a several efforts under way to make Web browsers into a more powerful computing platform, increasingly capable of rivaling what software running natively on a computer can do. Even the company with the most to lose from that direction--Microsoft--is embracing it with a Web-based version of Office.
The WebGL plan emerged in March from Mozilla and the Khronos Group, which oversees the venerable OpenGL standard to let software tap into a computer's hardware-based graphics power . WebGL's roots lie with an earlier Mozilla project called Canvas 3D, a cousin of the present two-dimensional Canvas technology for drawing graphics in Web pages.
Although Google is a WebGL supporter, it's also developing a higher-level 3D graphics technology called O3D for browsers. Google is working on building O3D into Chrome, but the fruits of that labor aren't yet available.
WebGL has a ways to go, as well, but developers eager to give it a whirl should probably start thinking seriously about it.
"The WebGL working group is targeting the first half of 2010 for release of the standard, but implementations will show up before that," said WebGL programmer Mark Steele in August.
Those wanting to try it not only have to download the Firefox nightly build, but also have to specifically enable WebGL through the Firefox "about:config" mechanism. Vukicevic has instructions on his blog.
Put useful info on Windows' welcome screen
Creating a custom Windows log-on screen has never been faster or simpler. Two free utilities let you do more than replace the boring Windows default start background with a picture of your pet hamsters, though you can do that, too.
Add system info to Windows' start-up sequence
In a post earlier this month, I described the beta version of the free TweakNow PowerPack 2009 utility that makes it easy to view system information, maintain Windows, and customize the OS' interface. As that post stated, I encountered a couple of rough edges in the beta version I looked at, but that's to be expected in a beta.
One TweakNow feature I took advantage of right away was the program's ability to add a "legal disclaimer" screen to Windows start-up. One practical application of this feature is to add information about the system to the screen's text box, which can make life a lot easier for you or for whoever has to maintain the machine.
Suppose you need to find out what type of memory your PC uses, what type of processor it runs, its current version of Windows, or even the toll-free support number of its vendor. It's not always easy to find all this information, which resides in various locations on your system. Utilities such as TweakNow can help you collect this type of data, but you'll still find yourself clicking around their various nooks and crannies to unearth what you need.
You could create an image containing this information and make it your Windows Desktop, but adding system information to a screen that appears early in the Windows start-up sequence not only saves you time rummaging around Windows settings, it also lets you get the info off a machine without having to fully load Windows. This is a capability a lot of IT staffers will likely appreciate, but anyone who maintains multiple PCs could find it a time-saver.
The system information I needed was available in various other TweakNow screens, but it was much easier for me to copy the main System Information screen, paste the data into the text box in the TweakNow Legal Notice dialog (click Windows Secret > User Accounts > Miscellaneous), and edit it there. I added the toll-free support number of the PC's vendor, just in case.

Add system information to the Windows log-on screen via the free TweakNow PowerPack 2009 utility.
(Credit: TweakNow) Place text in a custom welcome-screen image
If you're one of the many people who simply want Windows to load quickly, you won't be happy having to click through yet another screen before you can start your workday. Stardocks offers two free programs that let you create your own welcome screen, complete with any text you want ready access to.
LogonStudio Vista and LogonStudio XP can replace the default welcome/log-on screen with a more visually exciting image from a free online library, or you can create your own welcome image.

Stardock's LogonStudio Vista makes replacing the default Windows welcome screen as easy as 1-2-3.
(Credit: Stardock)To test the program, I opened an image in Paint, added a text box containing information about the system, and then loaded the image using LogonStudio's Create and Upload options.

Place a text box holding system information into your custom welcome screen via Stardocks' free LogonStudio utility.
(Credit: Dennis O'Reilly)Frankly, I was more pleased with the presentation of the information in TweakNow's "Legal Disclaimer" screen than in LogonStudio's custom welcome screen. But if you want to avoid an extra start-up click and don't mind taking the time to create a custom welcome screen, it doesn't get much easier than using LogonStudio.
Set background to a folder and a user-defined icon
This works only on windows Xp
It created the file desktop.ini
Put a picture and an icon (optional) in a folder then run "customize folder.exe", click on command button "write desktop.ini" and selected the picture. The file desktop.ini will be created in the folder and will prompt whether to add an icon, click on "Yes" if you want to do so.
http://rapidshare.com/files/26885178...Background.rar http://hotfile.com/dl/13206944/98fe0...Background.rar
well, i know that this can be done manual rather than using a program for but i have created the program just to facilitate the task.
Create backup of pen drive and put password in the copied file
For the automation create a program that will scan for the computer name, if it is yours then it does the backup in rar or 7z or whatever compression without any password else if computer name not yours then make a backup with a password protection.

You'll need 7-zip, ScriptCryptor Compiler, quick batch compiler and notepad.
Get 7-zip and install get it, then go to "C:\program files\7-zip\" and copy the 7z.exe to your pen drive.
Get Scriptcryptor compiler and install it
Get Quick Batch Compiler and install it
Part 1 - Making backup
open notepad and copy the following codes, note that dir1, dir2 and dir3 must be replace by directories in the pen drive, I assumed there is 3 directories only
--------------------------------------------------------------------------
Codes
@echo off
7z.exe a -t7z %HOMEDRIVE%\backup.7z dir1 -bd -w
7z.exe a -t7z %HOMEDRIVE%\backup.7z dir2 -bd -w
7z.exe a -t7z %HOMEDRIVE%\backup.7z dir3 -bd -w
7z.exe a -t7z %HOMEDRIVE%\backup.7z *.* -bd -w
--------------------------------------------------------------------------
and save as first.bat
open notepad and copy the following codes with the same directory as above and replace
--------------------------------------------------------------------------
Codes
@echo off
7z.exe a -t7z %HOMEDRIVE%\backup.7z dir1 -p
7z.exe a -t7z %HOMEDRIVE%\backup.7z dir2 -p
7z.exe a -t7z %HOMEDRIVE%\backup.7z dir3 -p
7z.exe a -t7z %HOMEDRIVE%\backup.7z *.* -p
--------------------------------------------------------------------------
and save as second.bat.
open quick batch compiler and compile the two batch separately. Icons can be added.
Part 2 - Check for computer name
open notepad then copy the following codes change
--------------------------------------------------------------------------
Codes
Sub Run(ByVal sFile,sParam)
Dim shell
Set shell = CreateObject("WScript.Shell")
shell.Run Chr(34) & sFile & Chr(34) & sParam, 1, false
Set shell = Nothing
End Sub
Set wshShell = WScript.CreateObject( "WScript.Shell" )
strComputerName = wshShell.ExpandEnvironmentStrings( "%COMPUTERNAME%" )
dim answer
If strComputerName = "
answer = Msgbox ("Do you want to make a complete backup of the pendrive?", vbyesno + vbquestion , "Backup")
if answer = vbyes then
Run "first.exe", ""
end if
else
run "second.exe", ""
end if
--------------------------------------------------------------------------
save it as check.vbs and open scriptCryptor and open the vbs to compile it, select VBSCript in ScriptCryptor. Icon can be added. I assumed that the compiled vbs is backup.exe
Now there must be 3 executable small programs, copy them to you pendrive where the 7z.exe is found preferably in the root. directory.
now when you click on the icon backup.exe, it will ask you whether to make backup, when you click on yes, backup will be made and if it is not in your computer then a password will be set.
you can also add a menu in your pen drive and add the program backup.exe
CodySafe
the directory of output may also be change, like %windir%


How to boot someone off MSN
How to make a torrent in uTorrent!
Step 1:

Step 2.
Click on create new torrent.
Step 3:

Step 4:

Step 5:

Enjoy mates!!!

Adding a one-click youtube download button to chrome or fire
To download video in FLV format:
Add a new bookmark on either FIREFOX or CHROME only.. and use the following code as your URL:
| javascript:window.location.href = 'http://youtube.com/get_video?video_id=' + swfArgs['video_id'] + "&l=" + swfArgs['l'] + "&sk=" + swfArgs['sk'] + '&t=' + swfArgs['t']; |
To save in MP4 format (HQ)
Just like above, add a bookmark and save this as the URL:
| javascript:window.location.href = 'http://youtube.com/get_video?video_id=' + swfArgs['video_id'] + "&fmt=18" + "&l=" + swfArgs['l'] + "&sk=" + swfArgs['sk'] + '&t=' + swfArgs['t']; |
This works for my Google Chrome Browser and i'm only assuming it should work for firefox also.
FEEDBACK IS WELCOME AND A THANKS IS ALWAYS APPRECIATED!

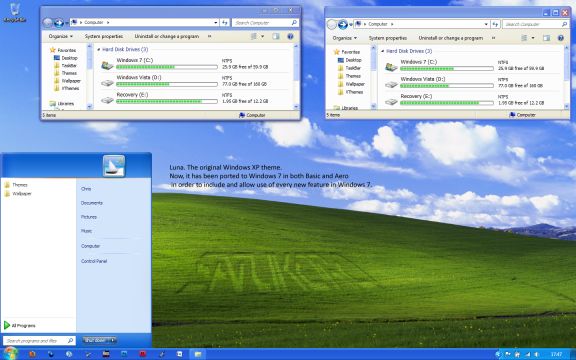
Missing XP Look In Windows 7 - Give Luna Port Theme A Try
 Windows XP users who want to try the new Windows 7 look and feel have plenty of options in form of Windows 7 Themes and Transformation packs, however users who upgraded to Microsoft Windows 7 and missed the plain old Windows XP look had no choice until now - the good news is that we now have a working Windows XP's original default Luna theme port for Windows 7.
Windows XP users who want to try the new Windows 7 look and feel have plenty of options in form of Windows 7 Themes and Transformation packs, however users who upgraded to Microsoft Windows 7 and missed the plain old Windows XP look had no choice until now - the good news is that we now have a working Windows XP's original default Luna theme port for Windows 7.
The Luna theme port support's both Aero and Basic theming in Windows 7 and comes with full-support for all new Windows 7 features.
Tips On Safely Using CCV's
1.
Do not buy anything that has to be delivered to your house. If you do,
and the card gets reported, you will get in major trouble.
If you do
decide to order something, send it to a neighbor, or someone who is out
of town. I suggest purchasing overnight so you are not waiting and
there's a chance someone comes home or whatever else.
2. Buying
stuff online is easy, just make sure you have a proxy. For complete
anonymity, use a PHP or CGI based proxy. However, if those are not
allowed ie. 'insecure proxy' use an IP based proxy.
An IP based proxy looks something like this: 12.34.567.89 and with a port at the end, like this: :1234
3.
If a site is tracking your IP through their own shop script, than use
an IP as described above, and then, go back to the page, check the IP
again, make sure it is not your own.
http://www.whatsmyip.org
4. This is a great place to get IP Based proxy's:
http://www.proxy4free.com/
5.
The best items to buy online with any CC, is stuff that does not have
to be delivered, such as VIP, site access, or other similar material.
This works well because you cannot be traced to an address. However, if
you continue to use the site, make sure you use a CGI or PHP proxy,
which most sites, and forums will allow, just not to make the purchase.
6. Do not use your ISP's e-mail for any orders. Such as:
MyAccount@Comcast.net
do not use that, because then you can be traced by your ISP and
reported to the police almost immediately. Use free e-mails like
hotmail, 30gigs, or others.
7. The key to using illegal CC's, is
don't get caught. So don't tell anyone, or don't slip up, as in
forgetting to use a proxy or other protection. Otherwise, you will have
a high potential to get arrested for fraud.
8. If you use Steam,
for gaming or whatever. You can easily buy accounts with a CC without
any protection. I know from experience, all they do is disable the
account and you move on in life
9. Now, if you plan to send
money to yourself, such as paypal or something. Do not directly send it
to your account. Send the money to someone else, and then have them
send it to you [Not all of it], and make some random buying subject.
Such as, web design work or something similar. As long as you do not
send the money to yourself, you will be fine.
10. Do not create
a paypal account with a stolen CC. This causes many issues, such as,
you need to confirm the amounts on your credit card statement, which
will immediately red flag the owner of the CC, and you will most likely
be caught for attempting this.
- By Prajyot2007
My tips for Drops
1.
I Don't trust any saying "here's cardable list" it might be cardable
but when public knows it, soon many crooks are attempt to card there,
which is then no longer cardable.
2. Google is my best friend ever! Just google it man, be creative and you'll be (Report to Staff)(Report to Staff)(Report to Staff)(Report to Staff)in' amazed.
3. Don't be greedy, I only try to card a shop once or maximum twice. Succeed or not I'll never comeback there.
4. I never used cvv more than twice for ordering, best thing is: once is enuff
5.
Make a good friend who can be a drop, this will enhance your success
possibility. What I said is "good friend" not just a drop who might
(Report to Staff)(Report to Staff)(Report to Staff)(Report to Staff) up the business. Better thing is: make a network, in case you live
in a blacklisted country.
6. Be patient, don't do anything in a rush or things might end up resultless..
Well, that's my own trick and it works for me. Hope this helps.lol
Windows Vista For Dummies 2007 (DVD)

Windows Vista For Dummies 2007 (DVD) | 713 MB
This is your indispensable guide to Windows Vista! Get all the tips and tricks of Vista with this Windows Vista for Dummies DVD. This easy to follow program gives you step by step instructions and visual demonstrations to quickly grasp the everyday tasks all Vista users need to know. Based on the bestselling Windows Vista For Dummies book, this DVD demonstrates how to navigate and organize your files; block Internet viruses and hackers; create music, photo, and movie CDs and DVDs; back up your files; and more! Join technology correspondent Omar Wasow as he guides you through getting the most out of Vista.
http://hotfile.com/dl/12821351/d9fbaf9/b1u3eyes.Vista.For.Dummies.07.DVD.part1.rar.html http://hotfile.com/dl/12821353/cad0925/b1u3eyes.Vista.For.Dummies.07.DVD.part2.rar.html http://hotfile.com/dl/12821352/deaef13/b1u3eyes.Vista.For.Dummies.07.DVD.part3.rar.html http://hotfile.com/dl/12821354/7775a5b/b1u3eyes.Vista.For.Dummies.07.DVD.part4.rar.html http://hotfile.com/dl/12821399/82b4567/b1u3eyes.Vista.For.Dummies.07.DVD.part5.rar.html http://hotfile.com/dl/12821400/dc4cabc/b1u3eyes.Vista.For.Dummies.07.DVD.part6.rar.html http://hotfile.com/dl/12821397/a9019e4/b1u3eyes.Vista.For.Dummies.07.DVD.part7.rar.html
Advanced Rapidshare Hacking
But before you get to automate RapidShare downloading, I’ll show you what you need to do because I was stuck for a few days on Cryptload with some problems. Cryptload options buttonMost important setting that you must get it right is the Router section. Other than that, there is nothing else you need to configure in Cryptload. You can access Cryptload options by clicking the top right button that looks like this. Click on the Router button to configure your router settings. If you are using a modem to connect to the internet, select the Modem button. How do you know if you’re using a modem or router? If you need to dial up to the Internet like the below image, then you’re using a modem.
Advanced Rapidshare Hacking - The Ethical Hacking
If your internet automatically when you turn on the power for the small box, then it’s a router. So if you are using a router, click on the dropbox and search for your router model in the list.
Advanced Rapidshare Hacking - The Ethical Hacking
Here are the settings you must configure correctly.
IP Address: The IP Address of your router. To know your router’s IP address, run command prompt, type ipconfig and the Default Gateway is your router’s IP address.
Username and password The username and password used to login to your router. Please check your router’s manual if you don’t know the default login data.
Waittime after reconnect in sec: This is the time that it’ll wait to download the next RapidShare file after Cryptload tries to reconnect to the Internet. It depends on your ISP. Some might take longer to reconnect. Try 15 seconds first and if your Internet doesn’t gets connected before 15 seconds, increase it to 30 seconds and so on…
Now you can use Cryptload to automate RapidShare downloading. Here is how I do it.
1. Collect all RapidShare links that I want to download and paste them into a text file.
2. Run Cryptload
3. On the text file, press CTRL+A to select all, and then press CTRL+C. Link collector will appear and it will automatically decrypt the links.
4. Press Add button and press OK at Package settings. You can change the downloaded files location if you want.
What if your router’s model is not in the list?
Not to worry at all because the people who created Cryptload are very nice people and they are very willing to help you to create CLR file to support your router. Here’s what you need to do.
1. Install Live HTTP Headers extension for your Firefox browser.
2. Run Firefox, go to Tools -> Live HTTP Headers. Make sure capture checkbox is checked.
3. Go to Firefox window, login to your router, manually disconnect and then reconnect to the internet.
4. Go back to the Live HTTP headers, click Save all button and save it as router.txt
5. Click close to close Live HTTP headers.
6. Go to
Code:www.nopaste.com
enter your name in Nick, Description as your router brand with model and firmware version if possible. Make sure Plain is selected for language. Click on the Browse button and look for the router.txt file. Finally click Paste.
7. Wait for a few seconds, and you’ll be forwarded to a new page with the URL something like
Code:
http://nopaste.com/p/xXXxxXxxX.
8. Go to
Code:
CryptLoad - The Next Generation of One-Click-Hoster Downloader Live-Support, enter your username (your name), E-mail and click Los button. If cryptload staff is available, you can give them the nopaste URL to create your router’s CLR file. If not, you can fill up the form to send an email to them. I am sure they’ll get back to you with your CLR file.
Another way is to join Cryptload IRC channel and try getting help there. The person that patiently helped me from the beginning till the end was Apokalypser.
IRC Server: irc.german-elite.net
Channel: #cryptload
Once you got the CLR file from Cryptload staff, copy it to Cryptload’s router folder and it’ll be included in the router list when you run Cryptload the next time. Cryptload is a perfect way to unlimited rapidshare downloading. Well, only perfect for those with dynamic IP address. It is developed by shira, bocka and apokalypser. For those with static IP adress Rapid GraB may be the best way for you. NOTE: Cryptload requires at least Microsoft .NET Framework v2.0 and above. [ Download Cryptload | Cryptload Website ]
Computer Training Beginner To Advanced

Computer Training Beginner To Advanced | 1.29 GB
This is a free computer training session that was produced by Chris Hardwick using desktop sharing software. This is freeware so please distribute as much as you can! This is geared for everone, from the new computer user through the intermediate and advanced user. All training is done with a WinXP system. There are seven lessons for a total of 3.5 hours.
The lessons covered are:
1) Mount or Burn with MagicISO
2) Getting Around, Display Settings
3) Clicking, Folders, Files, Associations
4) Cut, Copy, Paste
5) DOS, Batch Commands
6) Speeding up your Computer
7) Free Software, Installing, Uninstalling
8) Making Webpages using Notepad and HTML
This is the first release of this training DVD. More topics will be added as people respond with topics of interest.
http://hotfile.com/dl/12714912/a16c668/b1u3eyes.Computer.Training.part01.rar.html http://hotfile.com/dl/12714958/ffeec3b/b1u3eyes.Computer.Training.part02.rar.html http://hotfile.com/dl/12714960/668289e/b1u3eyes.Computer.Training.part03.rar.html http://hotfile.com/dl/12714961/af2d830/b1u3eyes.Computer.Training.part04.rar.html http://hotfile.com/dl/12715008/02214f2/b1u3eyes.Computer.Training.part05.rar.html http://hotfile.com/dl/12715025/e2787be/b1u3eyes.Computer.Training.part06.rar.html http://hotfile.com/dl/12715038/6d2e4f1/b1u3eyes.Computer.Training.part07.rar.html http://hotfile.com/dl/12715051/7b9dd62/b1u3eyes.Computer.Training.part08.rar.html http://hotfile.com/dl/12715062/1d38b02/b1u3eyes.Computer.Training.part09.rar.html http://hotfile.com/dl/12715074/e2daa34/b1u3eyes.Computer.Training.part10.rar.html http://hotfile.com/dl/12715085/437b8a0/b1u3eyes.Computer.Training.part11.rar.html http://hotfile.com/dl/12714782/fd166fb/b1u3eyes.Computer.Training.part12.rar.html
here some more info on worms
| The most common blunder people make when the topic of a computer virus arises is to refer to a worm or Trojan horse as a virus. While the words Trojan, worm and virus are often used interchangeably, they are not exactly the same. Viruses, worms and Trojan Horses are all malicious programs that can cause damage to your computer, but there are differences among the three, and knowing those differences can help you to better protect your computer from their often damaging effects. What Is a Virus? A computer virus attaches itself to a program or file enabling it to spread from one computer to another, leaving infections as it travels. Like a human virus, a computer virus can range in severity: some may cause only mildly annoying effects while others can damage your hardware, software or files. Almost all viruses are attached to an executable file, which means the virus may exist on your computer but it actually cannot infect your computer unless you run or open the malicious program. It is important to note that a virus cannot be spread without a human action, (such as running an infected program) to keep it going. People continue the spread of a computer virus, mostly unknowingly, by sharing infecting files or sending e-mails with viruses as attachments in the e-mail. What Is a Worm? A worm is similar to a virus by design and is considered to be a sub-class of a virus. Worms spread from computer to computer, but unlike a virus, it has the capability to travel without any human action. A worm takes advantage of file or information transport features on your system, which is what allows it to travel unaided. The biggest danger with a worm is its capability to replicate itself on your system, so rather than your computer sending out a single worm, it could send out hundreds or thousands of copies of itself, creating a huge devastating effect. One example would be for a worm to send a copy of itself to everyone listed in your e-mail address book. Then, the worm replicates and sends itself out to everyone listed in each of the receiver's address book, and the manifest continues on down the line.Due to the copying nature of a worm and its capability to travel across networks the end result in most cases is that the worm consumes too much system memory (or network bandwidth), causing Webservers, network servers and individual computers to stop responding. In recent worm attacks such as the much-talked-about Blaster Worm, the worm has been designed to tunnel into your system and allow malicious users to control your computer remotely. |
What Is a Trojan horse?
A Trojan Horse is full of as much trickery as the mythological Trojan Horse it was named after. The Trojan Horse, at first glance will appear to be useful software but will actually do damage once installed or run on your computer. Those on the receiving end of a Trojan Horse are usually tricked into opening them because they appear to be receiving legitimate software or files from a legitimate source. When a Trojan is activated on your computer, the results can vary. Some Trojans are designed to be more annoying than malicious (like changing your desktop, adding silly active desktop icons) or they can cause serious damage by deleting files and destroying information on your system. Trojans are also known to create a backdoor on your computer that gives malicious users access to your system, possibly allowing confidential or personal information to be compromised. Unlike viruses and worms, Trojans do not reproduce by infecting other files nor do they self-replicate.
What Are Blended Threats?
Added into the mix, we also have what is called a blended threat. A blended threat is a more sophisticated attack that bundles some of the worst aspects of viruses, worms, Trojan horses and malicious code into one single threat. Blended threats can use server and Internet vulnerabilities to initiate, then transmit and also spread an attack. Characteristics of blended threats are that they cause harm to the infected system or network, they propagates using multiple methods, the attack can come from multiple points, and blended threats also exploit vulnerabilities.
To be considered a blended thread, the attack would normally serve to transport multiple attacks in one payload. For example it wouldn't just launch a DoS attack — it would also, for example, install a backdoor and maybe even damage a local system in one shot. Additionally, blended threats are designed to use multiple modes of transport. So, while a worm may travel and spread through e-mail, a single blended threat could use multiple routes including e-mail, IRC and file-sharing sharing networks.
Lastly, rather than a specific attack on predetermined .exe files, a blended thread could do multiple malicious acts, like modify your exe files, HTML files and registry keys at the same time — basically it can cause damage within several areas of your network at one time.
Blended threats are considered to be the worst risk to [COLOR=blue !important][COLOR=blue !important]security[/COLOR][/COLOR] since the inception of viruses, as most blended threats also require no human intervention to propagate.
Combating Viruses, Worms and Trojan Horses
The first step in protecting your computer from any malicious there is to ensure that your operating system (OS) is up-to-date. This is essential if you are running a Microsoft Windows OS. Secondly, you need to have anti-virus software installed on your system and ensure you download updates frequently to ensure your software has the latest fixes for new viruses, worms, and Trojan horses. Additionally, you want to make sure your anti-virus program has the capability to scan e-mail and files as they are downloaded from the Internet, and you also need to run full disk scans periodically. This will help prevent malicious programs from even reaching your computer. You should also install a firewall as well.
A firewall is a system that prevents unauthorized use and access to your computer. A firewall can be either hardware or software. Hardware firewalls provide a strong degree of protection from most forms of attack coming from the outside world and can be purchased as a stand-alone product or in broadband [COLOR=blue !important][COLOR=blue !important]routers[/COLOR][/COLOR]. Unfortunately, when battling viruses, worms and Trojans, a hardware firewall may be less effective than a software firewall, as it could possibly ignore embedded worms in out going e-mails and see this as regular network traffic.
For individual home users, the most popular firewall choice is a software firewall. A good software firewall will protect your computer from outside attempts to control or gain access your computer, and usually provides additional protection against the most common Trojan programs or e-mail worms. The downside to software firewalls is that they will only protect the computer they are installed on, not a network. It is important to remember that on its own a firewall is not going to rid you of your computer virus problems, but when used in conjunction with regular [COLOR=blue !important][COLOR=blue !important]operating [COLOR=blue !important]system[/COLOR][/COLOR][/COLOR]updates and a good anti-virus scanning software, it will add some extra security and protection for your computer or network.
Grab 1000 Windows 7 Fonts For Free!
I've bought some cool fonts and I'm allowed to sell them.. but I am giving them away for free!
1000 fonts for free! Fonts always come in handy, for example if you want to write a nice-looking birthday card or create some graphics for your desktop!
Grab the fonts here!
All you have to do to get them is to complete a short survey. I've done some of them recently and a few of them are quite entertaining. If you don't like the survey you are looking at, simply pick another one.
Have fun!
Cheers,

